Platform > Ignite > BRAND intelligence
Flashpoint Brand Intelligence
In today’s digital landscape, protecting your brand has never been more challenging. The internet is rife with threats, from fraudulent domains to social media impersonations and mobile app scams. How can you safeguard your brand’s reputation and maintain customer trust?
With Flashpoint Brand Intelligence, you can easily monitor your brand’s critical assets, such as domains, logos, social media, and mobile apps, for abuse and impersonation and quickly mitigate any potential threats.

Detect and take action against brand attacks
Threat actors exploit reputable brands online to lend credibility to their attacks. They use look-alike domains, counterfeit websites, fraudulent social profiles, and even create fake mobile apps to target your brand. The consequences can be severe, ranging from customer distrust to significant financial losses. Most security teams have limited visibility into threat actors’ planning and attack techniques, resulting in valuable time spent identifying potential risks and leaving security teams scrambling to respond once the attacks are already underway. With Flashpoint Brand Intelligence, you can uncover real-time mentions of your brand, domains, and assets, allowing you to scale your operations and stay ahead of the evolving threat landscape.
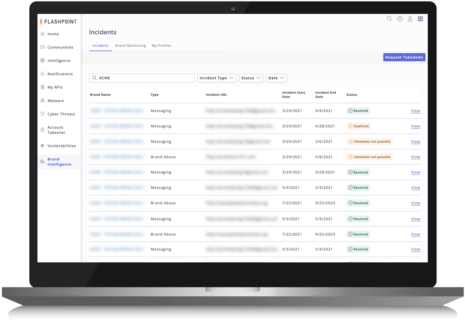
Early threat detection
Receive time-sensitive, contextual notification of malicious URLs targeting your organization and any affiliated brands so you can know whether to request a takedown.
Comprehensive monitoring
Get a holistic view of your organizations’ brand-related activity across various channels, including domains, social media, mobile apps, and more.
Streamlined incident response
Analysts investigate and review potentially malicious URLs on your behalf, minimizing false positives, and enabling easy incident resolution with one-click takedowns and reporting for rapid action and risk mitigation.
Helping you solve the most critical challenges facing your brand
Typosquatting
Detect against typosquatting and newly registered domains that pose risks by resembling official domains, often leading users to malicious sites.
Brand abuse
Identify brand abuse and the unauthorized use of trademarks or copyrights, undermining brand integrity and customer trust.
Phishing attacks
Triage phishing, smishing, and vishing threats before customers are tricked into revealing their sensitive information.
Fake mobile apps
Monitor trusted and third-party app stores to identify fraudulent and tampered apps before they damage your brand and compromise user data.
Social media impersonations
Prevent bad actors from creating profiles using your brand’s name and image to deceive followers and exploit trust for fraudulent purposes.
Takedowns
Swiftly initiate takedowns directly within the platform to remove fraudulent online content masquerading as your brand.
“Your team adds great value in every aspect of our brand protection, security investigations and threat intelligence programs. We are very happy with the services provided.”
–Head of Threat Management at a technology COMPANY
